PowerHuntShares : Easily scan network shares in your Active Directory domain
Table of Contents
I. Introduction
In this article, we'll discover and learn how to use a tool for enumerating and inventorying network file shares within an Active Directory domain.
The issue of network shares within corporate information systems is a complex one. Often very numerous and spread over dozens or hundreds of systems, the access permissions they possess and the legitimacy of their presence are often difficult to establish. For example, IT teams often struggle to answer the following questions:
- How many file shares are accessible via the network in your information system?
- Is it legitimate and necessary for the "Authenticated users" group to have read and write rights on a given share?
- Is such sharing still used by business teams?
These different examples are all potential attack vectors in a cyber attack.
As a pentester, I systematically perform an analysis of network shares when carrying out internal intrusion tests (an operation which consists in adopting the approach of an attacker). In 99% of cases, this analysis enables me to find interesting elements: shares accessible without authentication; with permissions that are too open; sensitive documents or documents containing passwords accessible to all authenticated users, etc.
The PowerHuntShares tool was created to help IT teams address this issue. The tool's objective is to provide an inventory and analysis of file shares and their permissions within an Active Directory domain. In particular, it identifies excessive privileges and "at risk" shares, and generates a web-based report that is easy to browse and use:
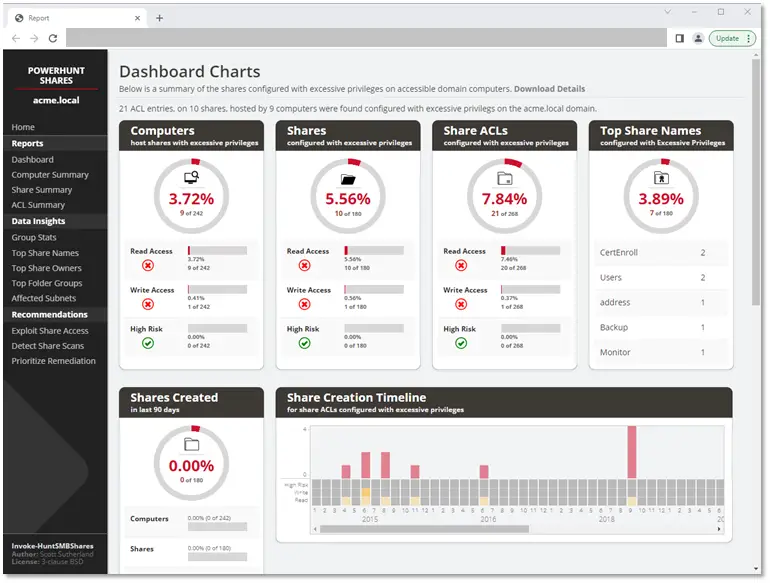
This tool was created by Scott Sutherland, who works for NetSPI.
II. Risks and definition of excessive privilege
A. What constitutes an excessive privilege?
Categorizing with certainty that a privilege is "excessive", i.e. that it grants more rights than necessary, is not an easy task.
First of all, we need to distinguish between SMB and NTFS rights. SMB rights apply to the network share and allow the user to access, read and/or modify its contents (sub-folders and files). NTFS rights, on the other hand, apply to the contents of a share (each folder, subfolder and file) and can thus further restrict permissions.
To better understand the difference between NTFS permissions and share permissions, please read our article on the subject:
Thus, a user may have read/write rights on a share, but be blocked from all folders on that share due to NTFS rights. However, there are some fairly classic cases of overly open permissions being set on shares, and these often stem from the following facts:
- The "Everyone" group is a direct reference that applies to both unauthenticated and authenticated users. In general, only a null session is required to access these resources.
- The "BUILTINUsers" group contains all authenticated domain users.
- The "Authenticated users" group contains all domain users on domain-integrated systems. This is why domain users can access a share when share permissions have been assigned to "BUILTINUsers".
Based on these first three principles, we can already define that an access permission granted to one of these groups is de facto excessive, since it applies to a group of people who a priori have nothing in common. With the exception of a few specific directories that would concern all trades and employees (emergency procedures, canteen menu, etc.), it is unlikely that this would be necessary for trade directories and files.
To get to the heart of the matter, you'll need to know your company's groups, organizational structure and hierarchy. This is, of course, beyond the scope of this article.
The risk of setting up more rights than necessary on a network share or folder is, in the first instance, data leakage. The greater the number of user accounts that have access to a shared directory, the greater the chance that one of them will be compromised, and that these rights will end up benefiting an attacker. This can lead to exfiltration of sensitive data or elevation of privilege (password discovery).
The case of ransomware or cryptolocker is of course worth mentioning: some ransomware not only encrypts local files on compromised systems and mounted shared directories. They can also seek out all shared directories on the information system and encrypt their contents. If all your shared directories are accessible by the user of the compromised workstation, the ransomware will take advantage of these open privileges to encrypt everything.
Another example of the risk of "internal" leakage is the case of a team trainee who decides to leave with all the company's internal tools and documents.
You should also be aware that write access to a folder can be a source of attack. It allows the attacker to drop malicious files in the hope that they will be executed, or even to booby-trap existing documents.
Also, simple write access to a folder can be used to steal credentials, from the moment a user opens a folder, without even consulting a single file. These attacks use files that are interpreted by "explorer.exe" (the Windows file browser) when a folder is consulted (display of a shortcut, icon, etc.).
An example of such an operation can be found in our article on the subject:
The main subject here is the attack surface, its control and reduction. By controlling share rights more precisely, you can reduce their attack surface.
Find out more about the attack surface in our dedicated article :
Finally, mapping, enumerating and searching for sensitive documents in network shares has its own TTP in the MITRE ATT&CK framework:
The PowerHuntShares script we're going to use performs an automated analysis of a domain's host network shares and their permissions, then produces a report in the form of a web page. This gives you a fairly exhaustive analysis, without any effort, and with a visualization of the results that speaks for itself.
PowerHunShares can use your current session if you're logged on to a domain-integrated system or a user account specified for it (out-of-domain cases or testing from a specific user). Here are its main functions:
- Authentication using your session or a specified account.
- Automatic discovery of domain-integrated systems from Active Directory, or use a list of hosts to be scanned if specified.
- List shares and collect ACLs (access permissions) for each share.
- Analysis and synthesis of collected data.
- HTML and CSV report generation.
Now let's take a closer look.
B. Analysis preparation and prerequisites
We're now going to learn how to use the PowerHuntShares PowerShell script to perform an analysis of our domain's network shares and their permissions.
You can download the PowerShell script from the following link:
The analysis can be performed from a domain-integrated system, as well as from a non-domain-integrated system. Simply adapt the options accordingly. Also, you need to choose carefully the user account you will use to run the analysis:
- If you want to have an exhaustive view of all the shared directories available on your domain, choose a user with high permissions on the domain so that nothing is missed.
- If you want to see exactly what rights and accesses a user or user population has, you need to use a user account that is a member of that population. You'll then get the real view of what they can access.
In all cases and for "classic" use, you don't need administrative rights, either at local system level or at domain level.
Once the script has been deposited on your system, you must first set the PowerShell execution policy to "bypass" to allow script execution (at the current session level), then import the script so that these functions can be used:
# Define bypass execution policy
Set-ExecutionPolicy -Scope Process Bypass
# Import module
Import-Module .PowerHuntShares.psm1Now you're ready to use PowerHuntShares!
C. Run a scan from a workstation in the domain
It's time to run our first scan. The easiest way to do this is, of course, to run it from a workstation within the domain, with a session opened by a valid user on the domain.
If the PowerHuntShares module is loaded in your PowerShell session, simply run the following command:
# PowerHuntShares analysis from a workstation and a domain session
mkdir C:Temptest
Invoke-HuntSMBShares -Threads 100 -OutputDirectory c:temptest
Here, you don't need to specify the domain name or IP address of the domain controller, as the workstation is already integrated into the Active Directory domain, and network and session information will be used. If you wish to analyze only certain hosts, simply create a list with a host (name or IP address) in a text file, then specify it after the"-HostList" option:
# PowerHuntShares analysis with current session and host list
Invoke-HuntSMBShares -Threads 100 -OutputDirectory c:\temptest -HostList c:\temphosts.txtWhile PowerHuntShares is running, you will see the progress of its scan in the terminal:
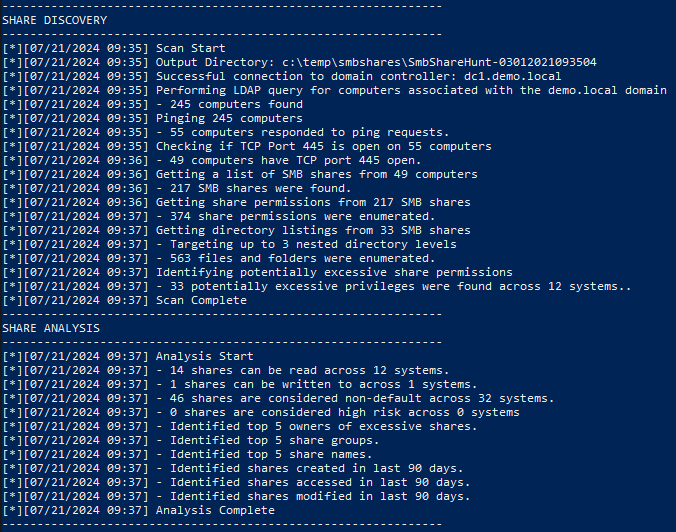
This information tells us what scans are in progress, how many systems and shares have been discovered, and so on. This output can be useful when analyzing information systems comprising a large number of hosts, as such an analysis can then take several hours. The "SHARE ANALYSIS" section deals with the aggregation, analysis and synthesis of the data collected. This is where we start to get some initial feedback on the discoveries made.
At the end of its execution, you will see a small summary in this same terminal:
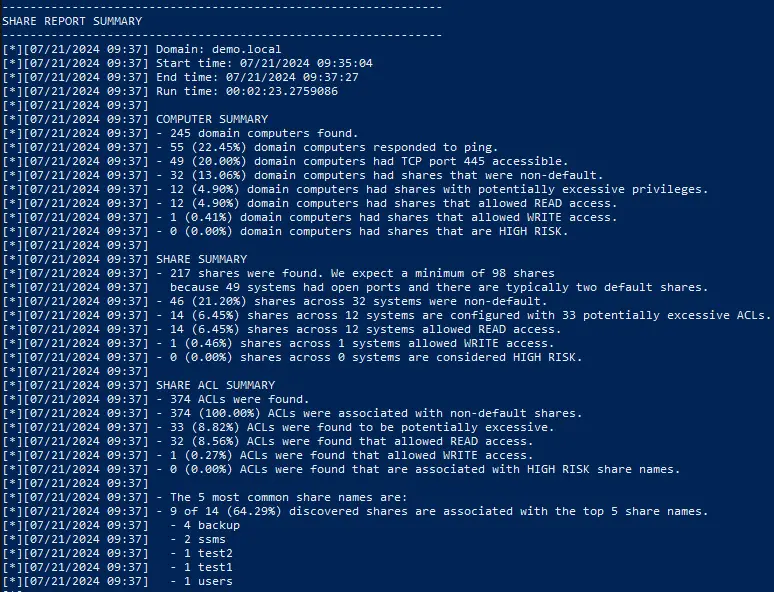
Here you'll find the main data collected and analyzed, including the number of shares with read and write permissions, those identified as sensitive ("C$","inetpub","wwwroot", etc.), with excessive permissions, etc.
This is only a summary, as the concrete, usable information is contained in the HTML report in the folder you specified at launch ("-OutputDirectory" option). We'll look at its contents in the next section.
- Change user
As we saw earlier in this article, it's entirely possible to analyze shares "from the point of view" of another user. This gives you a better idea of what he or she has access to. To do this, it is necessary to specify the user account after the "-Credentials" option:
# Analyse depuis un poste intégré au domaine avec un autre compte
Invoke-HuntSMBShares -Threads 100 -OutputDirectory c:temptest -Credentials domainuser
You will then be asked for the user's login and password once the order has been processed:
![]() D. Run a scan from an off-domain workstation
D. Run a scan from an off-domain workstation
We'll now look at how to use PowerHuntShares from a non-domain computer. To do this, we'll use the "-DomainController" options to specify the IP address or full name of the domain controller, and "-Credentials" to specify the user account to be used:
# Analysis from a workstation not integrated into the domain
Invoke-HuntSMBShares -Threads 100 -RunSpaceTimeOut 10 -OutputDirectory out -Credential it-connect.tech\LUANN_WARD -DomainController 192.168.56.102It's that simple! Once again, you'll need to enter the user's password, and can use the various options seen in the previous section.
We'll now turn our attention to the most interesting of all, the HTML and CSV report produced by PowerHuntShares, which summarizes the data collected. You'll find it in the folder you specified at launch ("-OutputDirectory" option):
Use the menu on the left to navigate through the various sections of the report:
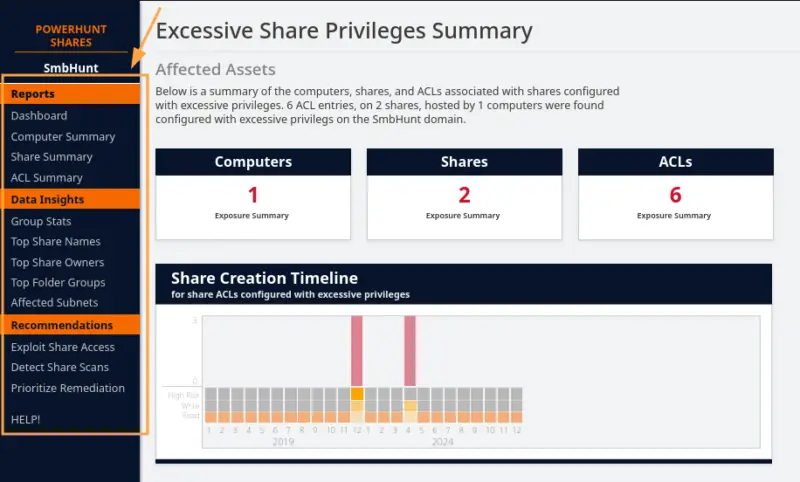
In the "Reports" section, the "Dashboard" tab gives you an overview of the analysis, with key elements such as the percentage of shares with read-only access, write access, the timeline for the creation of identified shares, and so on.
The "Computer Summary" tab contains the list of computers discovered and scanned, the list of those exposing network shares, those exposing read-only network shares, and so on.
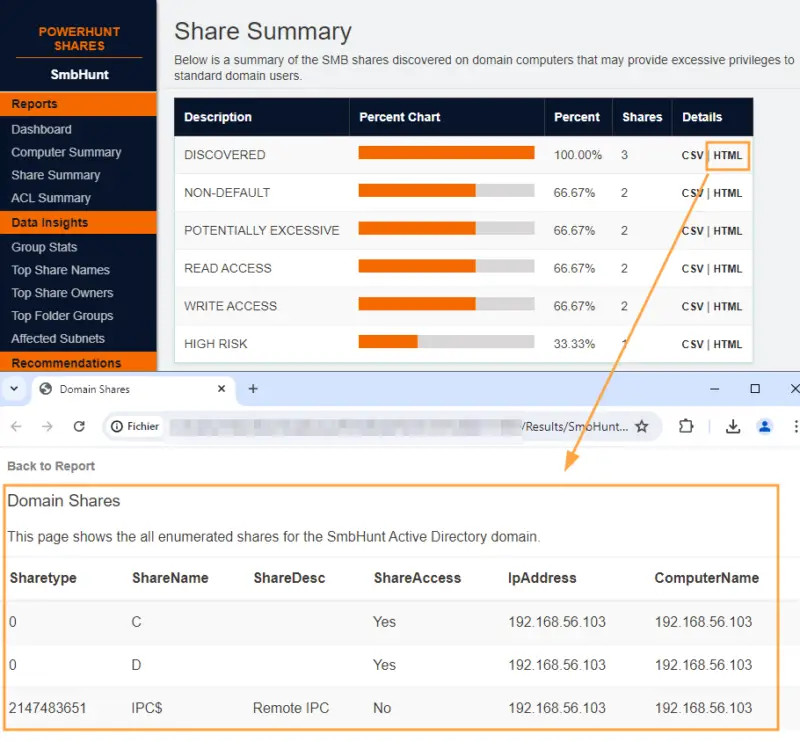
The "Share Summary" tab is surely one of the most interesting:
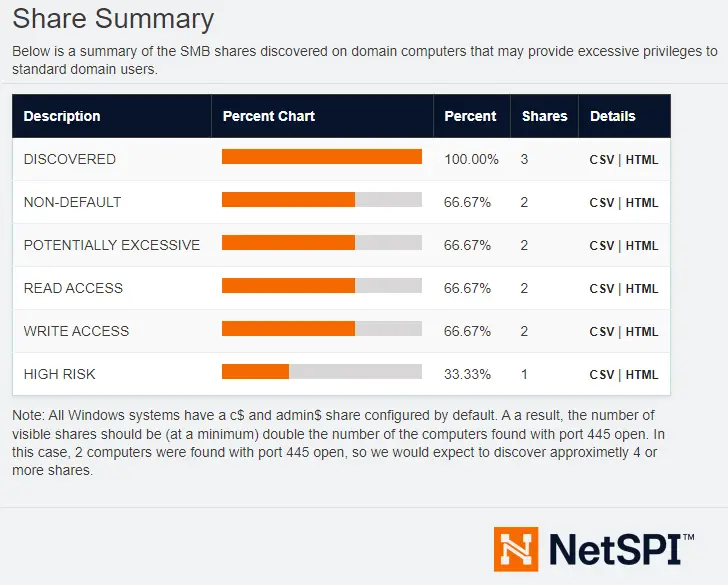
This is where you can actually see the excessive permissions identified by PowerHuntShares. Keeping in mind the user with whom the analysis was carried out:
- Discovered: contains all identified shares.
- Non-default: contains all shares that do not have a name common and usual on a Windows system (such as "IPC$").
- Potentially Excessive: lists all shares with ACLs on "generic" groups such as "Authenticated Users" or "Everyone", and more generally with potentially overly generous permissions.
- Read access: all shares with a read access ACL.
- Write access: all shares with a write access ACL.
- High risk: all shares with classic sensitive share names (such as "wwwroot", " C", etc.).
Then, depending on your security rules and business needs, you need to determine whether these accesses are legitimate or not, and then remove them. Here's an example of excessive privileges discovered on a share :
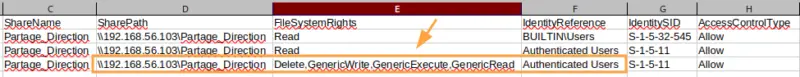
Here we can see that the "Authenticated Users" group, i.e. all authenticated users in the domain, have read/write access to the"Share_Direction" share, which seems abnormal.
Depending on the size of your domain and the security practices of your IT teams, you may have more or less results in the automated analysis. In any case, you'll need to manually check the details of these results and determine their legitimacy and importance.
The tabs in the "Data Insights" menu provide statistics such as the most frequently used share names, the main share owners, and the distribution of shares and ACLs by subnet. Here again, the aim is to provide an overview of the analysis, which may be of interest depending on your context.
Finally, each table offers the option of downloading selection details in HTML or CSV format, the latter being very useful for scripting or automated analysis:
The web report is clearly a welcome addition to the tool's strengths. It provides a different view, focusing on weaknesses concerning network share permissions. I encourage you to spend some time on this one, so as to fully understand each section, as well as each result, as the work involved can be quite substantial on medium-sized and large company information systems.
V. Conclusion
PowerHuntShares is a powerful tool for analyzing and inventorying network shares within an Active Directory domain. By automating the collection of permissions and generating detailed reports, it will enable you to better map and secure your network shares. The use of this tool, combined with a good knowledge of groups and permissions in your organization, can greatly reduce the security risks associated with network shares.
An important step to remember is to manually analyze the results and check the legitimacy of any permissions detected as excessive. Once you've mastered the tool, all you need to do is run a scan and analyze the results regularly.
To take this subject of network share security a step further, I invite you to discover the Snaffler tool. It enables you to search for sensitive data, such as passwords or business data, in the network shares of the systems in your domain:
 www.it-connect.fr
www.it-connect.fr









